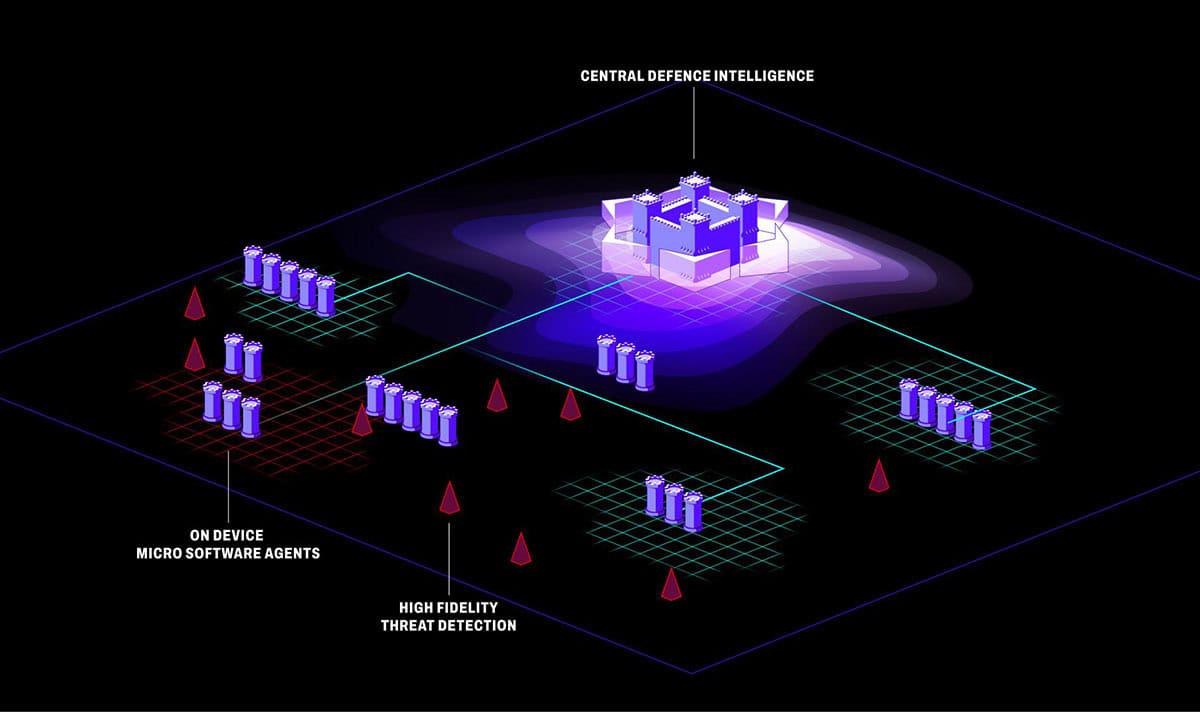
Periphery is a leading developer of advanced AI-powered cybersecurity threat management solutions for embedded military and defence systems.
Our technology protects the embedded computers—running Linux, RTOS, or Android—found in drones, autonomous vehicles, wearable devices, rugged network gateways, and other mission-critical IoT platforms. Designed specifically for complex and resource-constrained environments, our solutions defend against ever-evolving cyber threats across the lifecycle of defence assets.
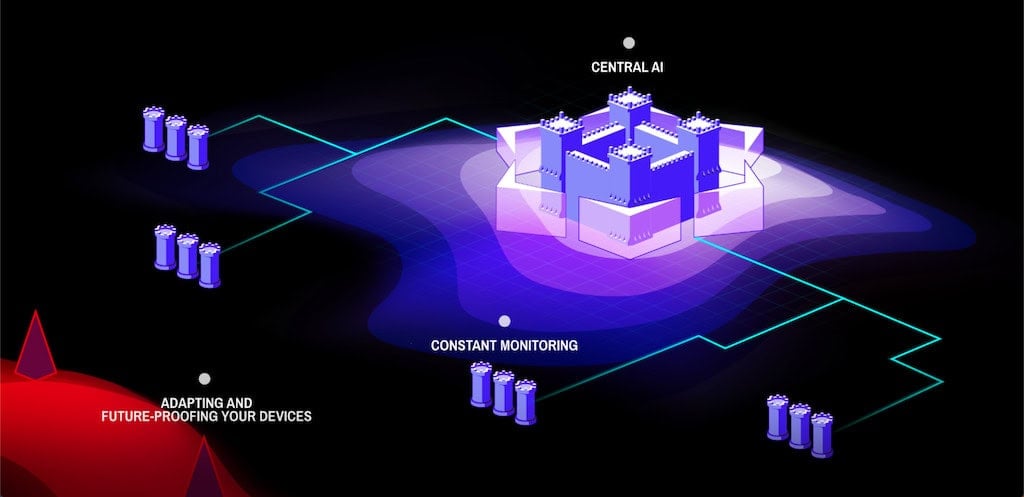
Periphery addresses the critical challenge of maintaining security and compliance in the field. Our tools allow embedded systems to be security-hardened both before and after deployment, ensuring resilience even in hostile or disconnected environments. Once deployed, devices continue to be monitored in real-time, enabling the immediate detection of anomalous behaviour or breaches—wherever they occur.
Founded by former NATO and BAE Systems engineers, Periphery brings deep expertise in securing complex, high-risk environments. Our founding team has spent decades working on the front lines of national security, where they identified the critical need for scalable, lightweight cyber defence tailored to embedded systems.
Today, Periphery operates internationally from its UK headquarters, working closely with defence partners to safeguard next-generation technologies across land, sea, air, and space domains.