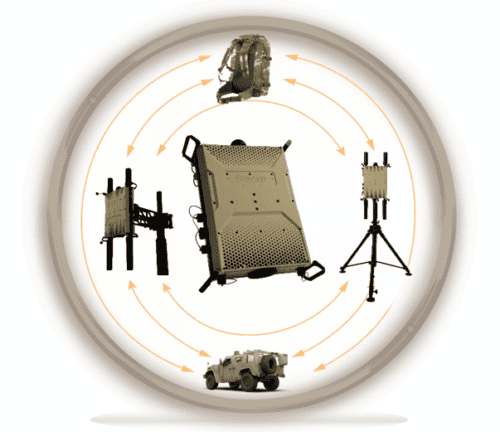
Drone cyber takeover technologies are a commonly used and pivotal element of military counter UAS (C-UAS) operations, providing non-kinetic solutions to the growing threats of drone attacks and surveillance.
With unmanned aerial systems (UAS) being increasingly deployed for reconnaissance, surveillance, and offensive capabilities, defense forces are incorporating cyber takeover as part of military anti drone technology frameworks to protect assets and ensure effective drone security.
A traditional anti drone system often relies on kinetic methods such as projectiles and explosives in order to intercept and destroy rogue drones. However, in environments where no-line-of-sight conditions prevail, kinetic counter drone systems may prove ineffective. Kinetic drone countermeasures may also produce hazards due to shrapnel and falling drones, posing a risk to personnel.
Drone cyber takeover methods bypass these issues by exploiting communication vulnerabilities, cutting the drone’s connection to its operator, and initiating remote-controlled drone takedown procedures. This technology can be indispensable in urban environments, dense battlefields, and scenarios where engagement risks are high.
Cyber takeover systems also provide a strategic advantage by neutralizing threats while preserving the drone’s structure and onboard data. This enhances intelligence gathering and situational awareness, allowing further analysis and reducing collateral damage.
Table of contents: